COVID-19 ATTACKS THE WEB

COVID-19 is being used in a variety of malicious campaigns including email spam, BEC, malware, ransomware, and malicious domains. As the number of those afflicted continue to surge by thousands, campaigns that use the disease as a lure likewise increase.
TYPES OF THREATS USING COVID-19:
When the malware executes, it will automatically restart the machine and then display a virus-themed window that cannot be closed. The usual exit button on the top right side of the window does not function
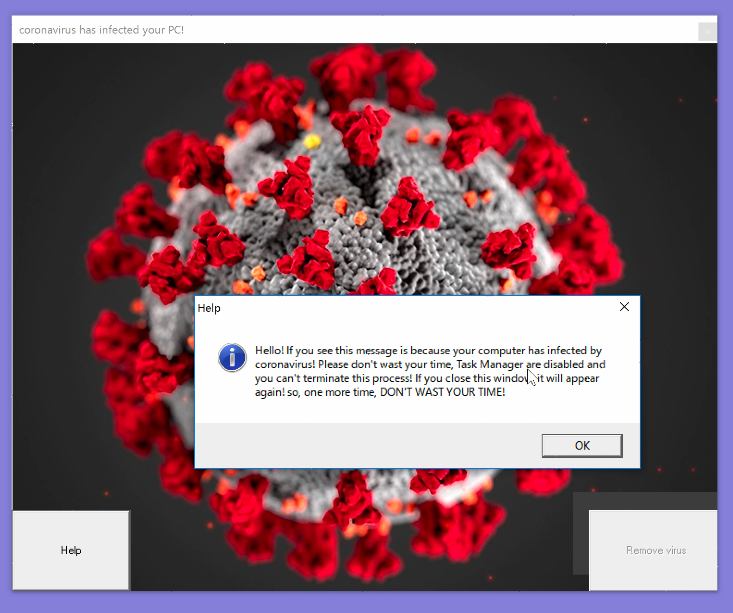
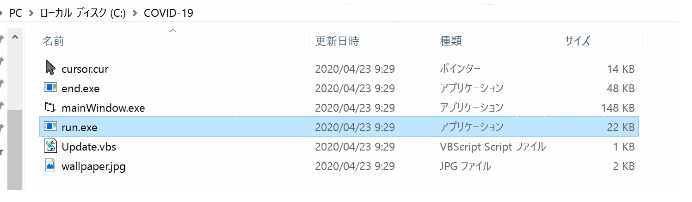
The malware also creates a hidden folder named “COVID-19,” which contains several secondary modules. Manually restarting the system will execute another binary file and display the grey screen.
3.Malicious Websites
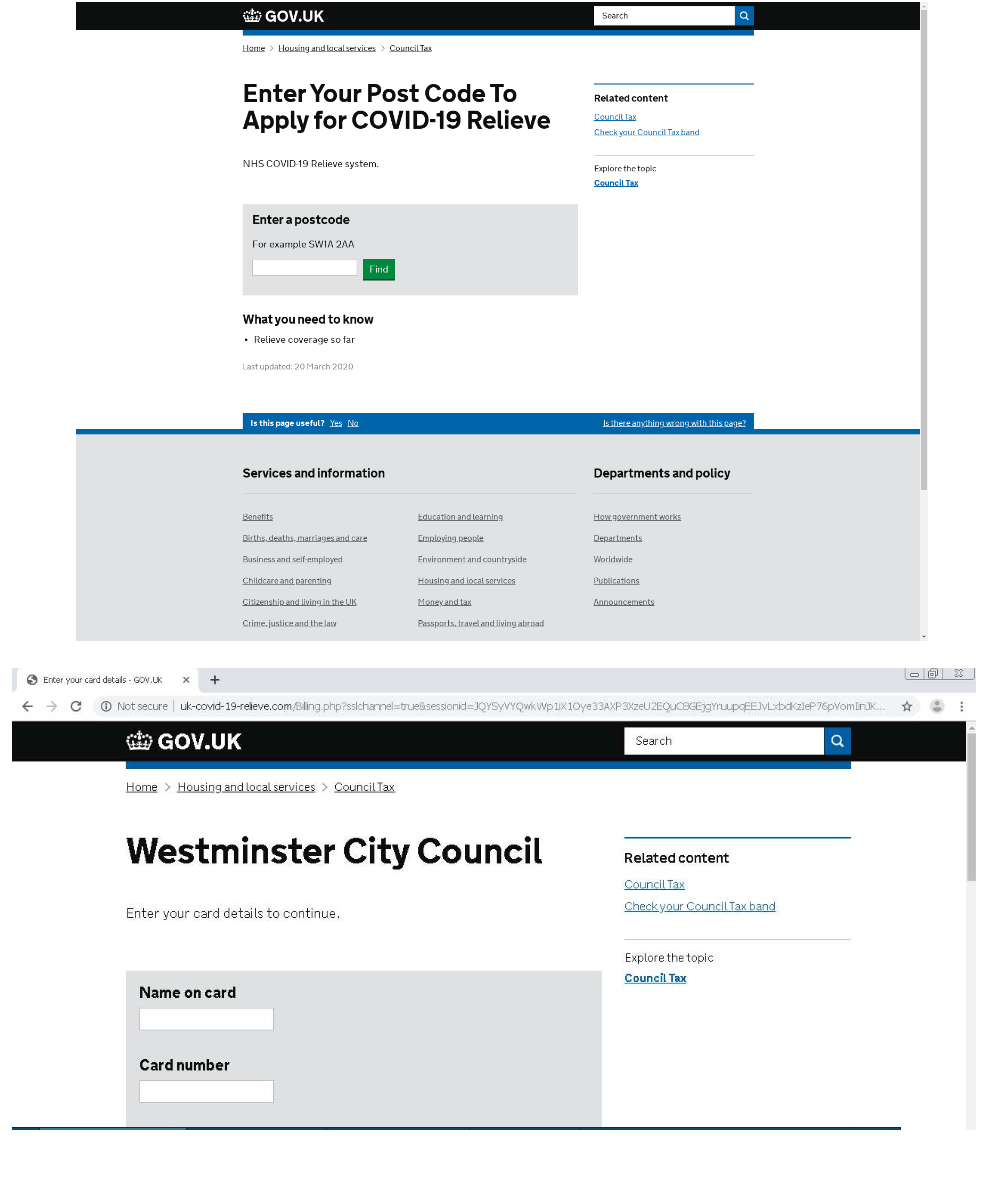
A fake government website has been spotted luring users with the promise of aid or relief. The domain uk-covid-19-relieve[.]com imitating legitimate "gov.uk" sites. It will ask for personal information and collect users’ bank account credentials if they enter a correct postcode.
Virus-related domains hosting malicious files are also still active. The site hxxps://corona-map-data[.]com/bin/regsrtjser346.exe loads the DanaBot banking trojan, which is capable of stealing credentials and hijacking infected systems.
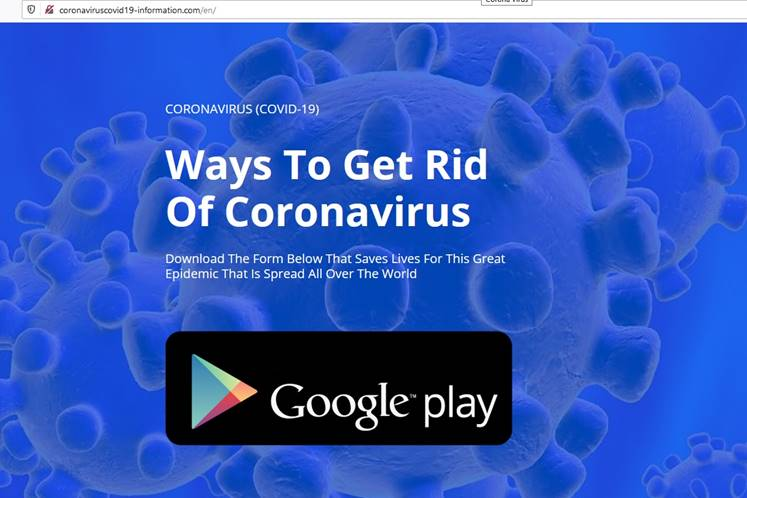
Another recent example is hxxp://coronaviruscovid19-information[.]com/en. The site encourages you to download a mobile application called “Ways To Get Rid of Coronavirus,” promising a cure.
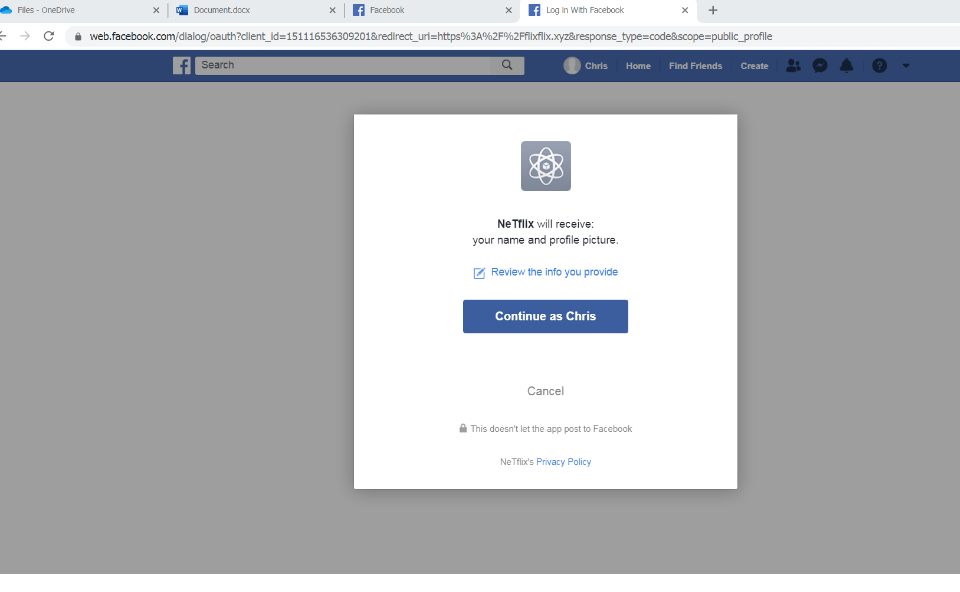
They use fake streaming sites, or sites offering entertainment promotions to appeal to users. It is spotted the domain hxxps://promo-covid19-neftlix[.]ml, which is actually a phishing site that steals Netflix account credentials. As always, users should always be mindful of websites they regularly use, and to keep credentials to online accounts as private as possible
A scam and phishing tactic circulating online via Facebook Messenger
First Scenario
If the user is already logged in to their Facebook account, it will simply continue and redirect to a fake Netflix page
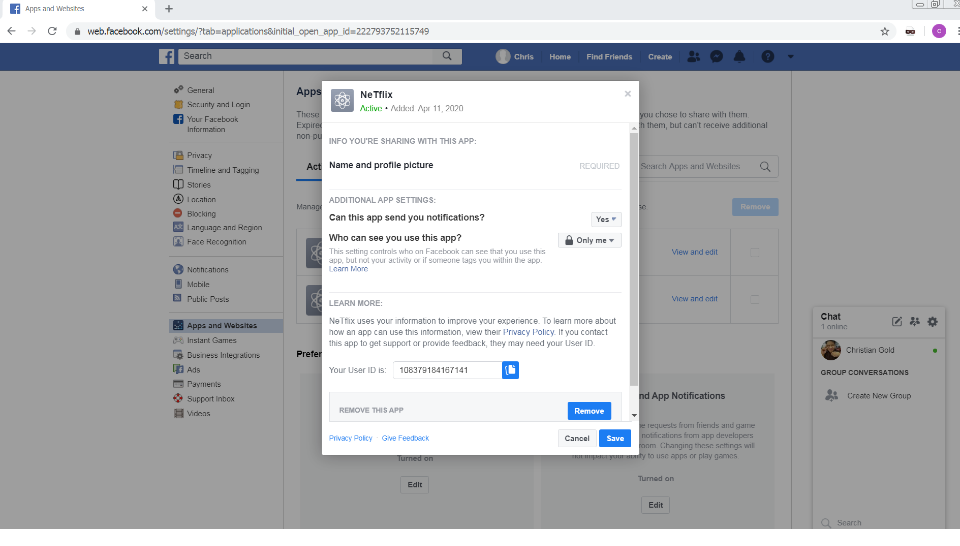
This page captures the victim’s Facebook login credentials and creates an active subscription to an app in Facebook named “NeTflix”. The app is simply an indicator that the user has already been compromised. If a user already subscribed to the fake app and clicks on the malicious link again, they will be redirected to a second page, detailed in the next section
Second Scenario
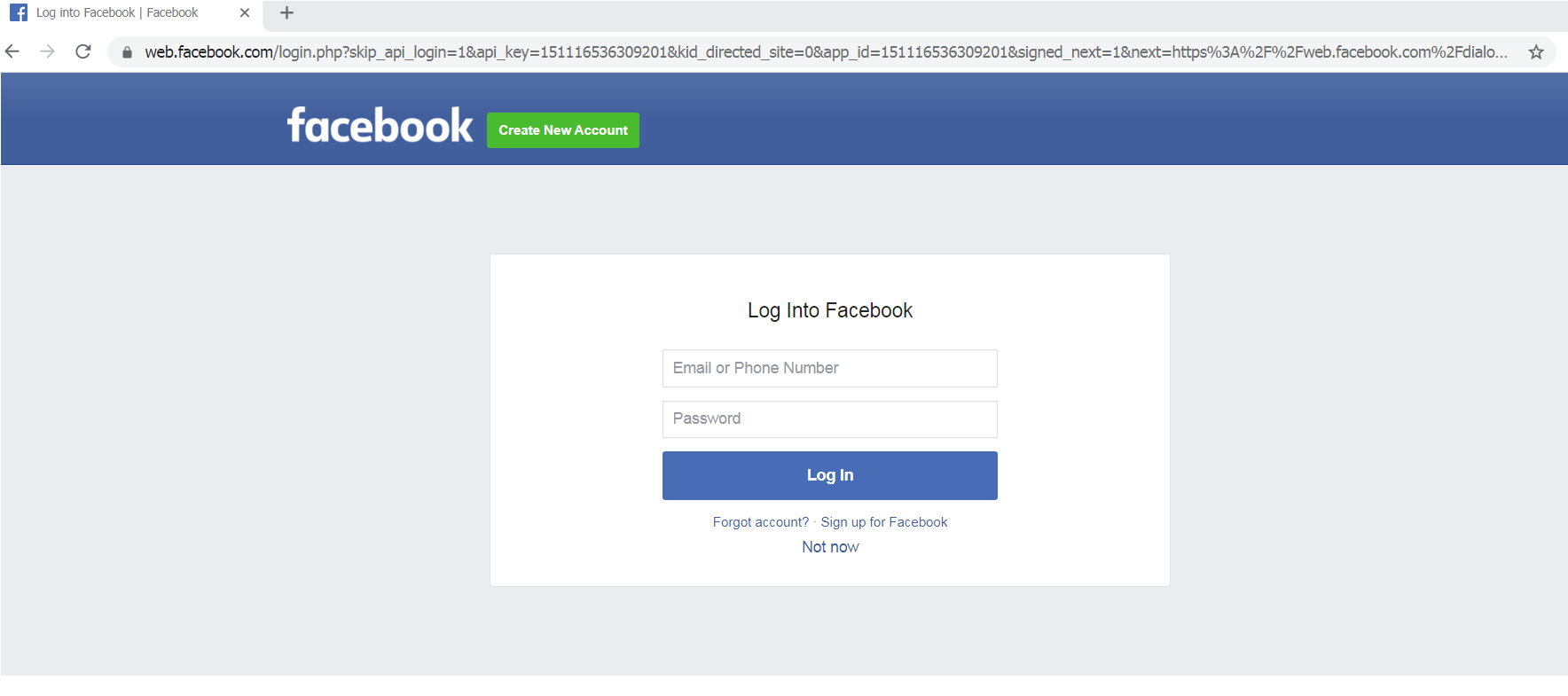
This is the second possibility for would-be victims. Users who have
not logged in to their Facebook accounts will be redirected to the
Facebook login page
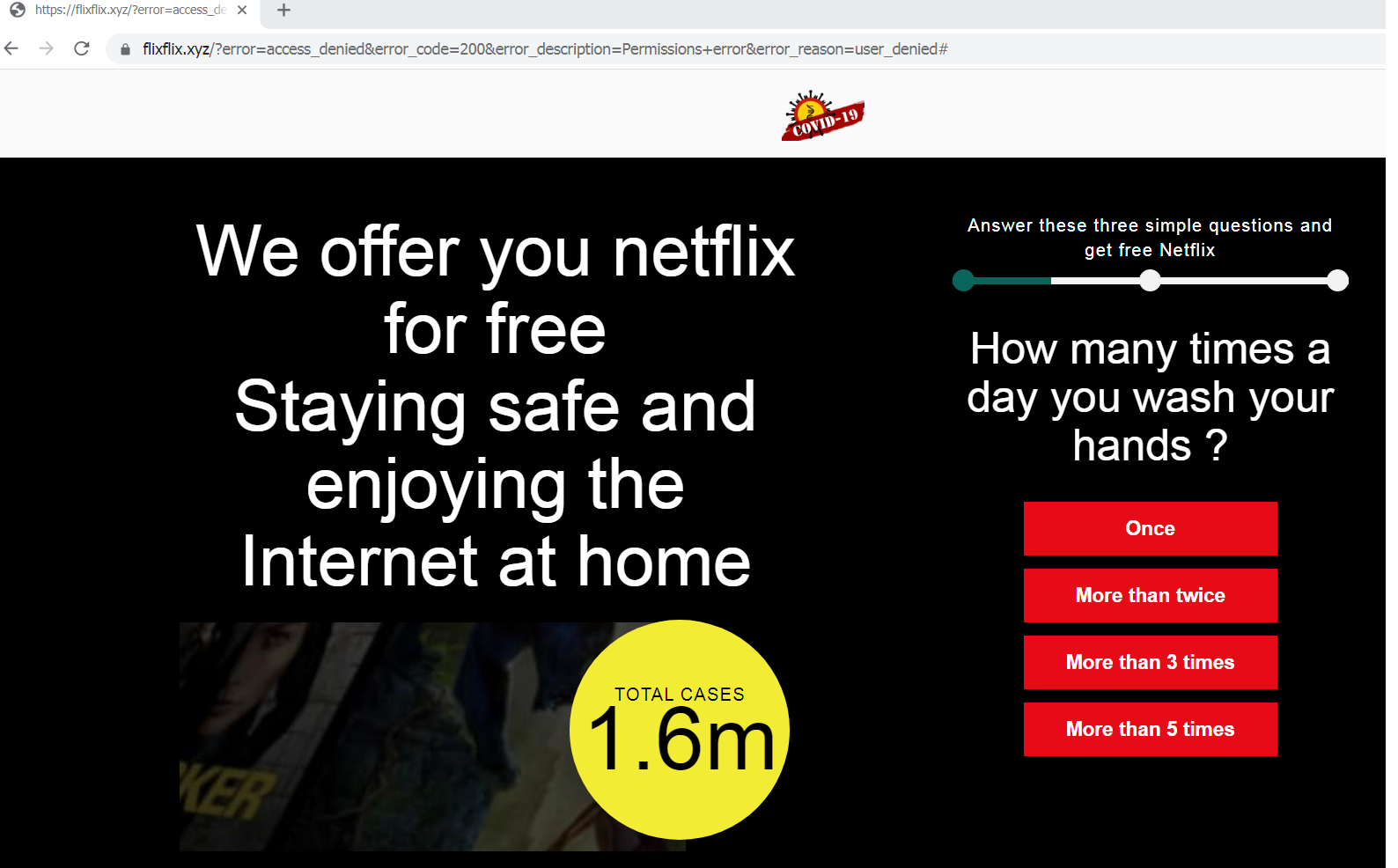
If the user enters their account credentials, it will redirect to the fraud page seen in the first scenario. If the user clicks the “Not now” button, it will redirect to the fake Netflix page, as seen below. The page contains a fake Netflix offer and a survey on the right side with questions about COVID-19 and cleanliness habits. The scammers used free, newly created domains unrelated to Netflix.
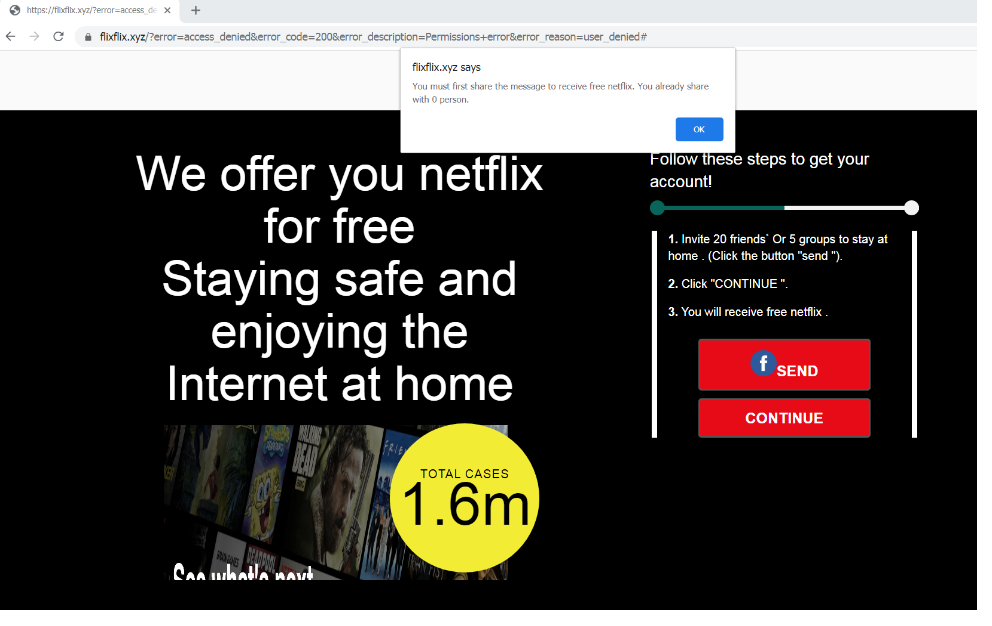
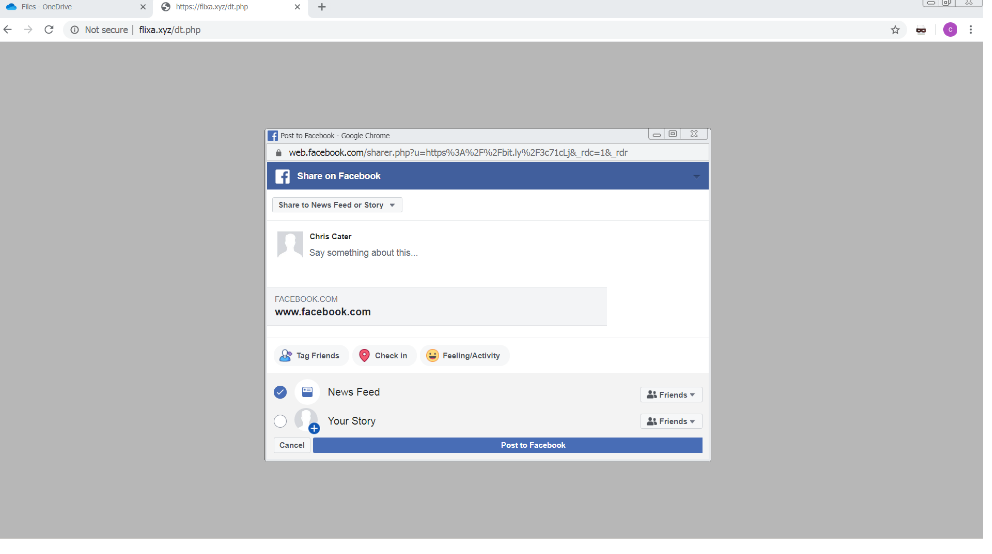
Regardless if users click the ‘Send’ or ‘Continue’ button at the end of the survey, it will redirect users to the same page — a Facebook share prompt. In this next step, users are urged again to spread malicious links by clicking a “Share” button for Facebook contacts. Then the user will be prompted to log in to Facebook
Users that enter their Facebook login credentials will be taken to an automatically generated post. Clicking on the “Post” button will post a status about the malicious link on the user’s Facebook page
These two scenarios show that whether the user is already logged in or refuses to give their credentials, they will be pressured into sharing fraudulent links.These evidences are enough to show that how easily you can breach websites and steal credentials by malicious URL redirects and use Credential stuffing attacks to gain even more control over user's other accounts. So try to be extra cautious while making payments especially to a COVID relief fund, make sure that you fully trust it and shows you a proof of donation.






0 Comments