What is DDOS Attack?
Basically DDOS stands for Distributed Denial Of Service ,this cyber attack maliciously attempts to disrupt the normal traffic of a targeted server , service or a network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
Its like an unexpected traffic clogging up the highway , stopping the regular traffic from arriving its destination.
Probable motivation for DDOS attacks are:
* Ransom
* Targeted attacks
* Hacktivism
* Boredom
Few of the most vulnerable and dangerous DDOS are The Google Attack in 2017 , The AWS DDOS attack in2020 , GitHub attack in 2018 and the Mirai Dyn attack in 2016
----------------------------------------------------------------------------------------------------------------------------
Types of DDOS Attack:
- Volume base attacks
The goal of this type of attack is to overload the website's bandwidth or cause damage to CPU or IOPS usage issues. This type of attack is easily achieved by the attackers since most website owners are leveraging shared hosts. This attack is usually measured in bits per second (BPS).
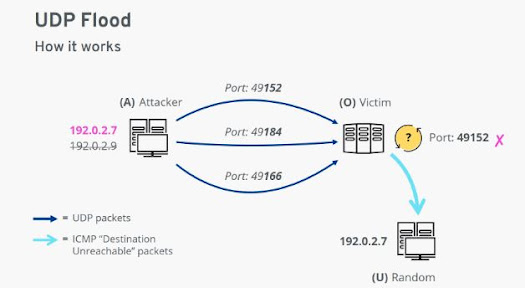
- UDP flood
The User Datagram Protocol (UDP) DoS will flood various ports at random, this protocol is used to generate error messages to the IP address when problems prevent IP packets delivery.
- ICMP flood
The Internet Control Message
Protocol flood overwhelms the target resource with ICMP Echo Request (ping) packets,
generally sending packets as fast as possible without waiting for
replies.
This type of attack can consume both outgoing and incoming bandwidth, since the
victim’s servers will often attempt to respond with ICMP Echo Reply packets,
resulting a significant overall system slowdown.
- Ping of Death Attack
Attacker attempts to crash, destabilize, or freeze
the targeted computer or service by sending malformed or oversized packets
using a simple ping command.
The size of a correctly-formed IPv4 packet
including the IP header is 65,535 bytes, including a total payload size of 84
bytes
Sending a ping packet larger than 65,535 bytes
violates the Internet Protocol ,ends up with an oversized packet, memory
overflow could occur and lead to various system problems including crash
2.Protocol / Network layer attacks
-SYN Flood (Synchronize)
This attack aims to make a server unavailable to legitimate traffic by consuming all available server resources. By repeatedly sending initial connection request (SYN) packets, the attacker is able to overwhelm all available ports on a targeted server machine, causing the targeted device to respond to legitimate traffic sluggishly or not at all.
It is a type of TCP(Transmission Control Protocol)-state exhaustion attack
3.Application layer attacks
-HTTP Flood
The attacker makes what appear to be normal interactions with a web server or application. All of the interactions come from web browsers to look like regular user activity, but they're coordinated to use up as many resources from the server as possible.
HTTP floods do not use malformed packets, spoofing or reflection techniques, and require less bandwidth than other attacks to bring down the targeted site or server.
Unintentional Denial Of Service:
An unintentional denial-of-service can occur when a system ends up denied, not due to a deliberate attack by a single individual or group of individuals, but simply due to a sudden enormous spike in popularity.
Example : When Michael Jackson died in 2009, websites such as Google and Twitter slowed down or even crashed. Many sites' servers thought the requests were from a virus or spyware trying to cause a denial-of-service attack, warning users that their queries looked like "automated requests from a computer virus or spyware application".
---------------------------------------------------------------------------------------------------------------
Ways to protect from DDOS attack:

Notifying ISP
When your is under attack, you should notify your ISP provider as soon as possible to determine if your traffic can be re-routed. Having a backup ISP is also a good idea. Also, consider services that disperse the massive DDoS traffic among a network of servers rendering the attack ineffective.
Internet Service Providers will use Black Hole Routing which directs traffic into a null route sometimes referred to as a black hole(non-existent server) when excessive traffic occurs thereby keeping the targeted website or network from crashing, but the drawback is that both legitimate and illegitimate traffic is rerouted in this fashion.
Configure firewalls and routers
The initial line of defense would be keeping your routers and firewalls updated with the latest security patches. Firewalls and routers should be configured to reject bogus traffic.
A firewall is a barrier protecting a device from dangerous and unwanted communications.
Using artificial intelligence
AI programs could identify and defend against known DDoS indicative patterns. Plus, the self-learning capabilities of AI would help predict and identify future DDoS patterns.
The systems that can quickly route Internet traffic to the cloud, where it’s analyzed, and malicious web traffic can be blocked before it reaches a company’s computers.
Secure your Internet of Things devices:
To keep your devices from becoming a part of a botnet, it’s smart to make sure your computers have trusted security software.
If you have IoT devices, you should make sure your devices are formatted for the maximum protection. Secure passwords should be used for all devices. Internet of Things devices have been vulnerable to weak passwords, with many devices operating with easily discovered default passwords.
Upstream filtering:
In this method All traffic is passed through a
"cleaning center" or a "scrubbing center" via various
methods such as proxies, tunnels, digital cross connects, or even direct
circuits, which separates "bad" traffic (DDoS and also other common
internet attacks) and only sends good traffic beyond to the server.
The provider needs central connectivity to the
Internet to manage this kind of service unless they happen to be located within
the same facility as the "cleaning center" or "scrubbing
center".
---------------------------------------------------------------------------------------------------------------
Aftermaths of DDOS Attack:
- Website Downtime
- Server and Hosting Issues
- Website Vulnerability
- Lose of money and time
- An unreachable online platform
- Loss of confidential data
- Loss of productivity, for example an online portal
- Reputation damage of a brand.
We shall further discuss about other types of cyberattacks in upcoming blogs.












0 Comments