WHAT IS NETSTAT???
To see what linux says, type ‘man netstat’ in terminal and see the lines under the description heading.
It is a cross-platform command line network utility tool and does not feature a GUI. The easiest way of understanding of what netstat is, is from the name itself. It is derived from the words ‘Network’ and ‘statistics’ which implies that it delivers basic statistics on all network activities and informs users on which ports and addresses the corresponding connections (like TCP, UDP) are running and which ports are open for tasks.
NOTE: The parameters of netstat’s commands (as well as their outputs) differ from system to system, when it comes to their functions, the various implementations are very similar. Here, I have used kali linux.
SYNTAX:
netstat [OPTIONS]
WORKING OF OPTIONS:
POSSIBLE FIRST OPTIONS OF NETSTAT:
The first arguments can be either -r, -g, -i, -M, -s or none.
OPTIONS:
The options other than the first options (mentioned above) in the table acts as a constraint or defines the behaviour of the output.
Let’s see the output of some of the basic commands of netstat.
Code
$ netstat -a
Shows all ports.
Code
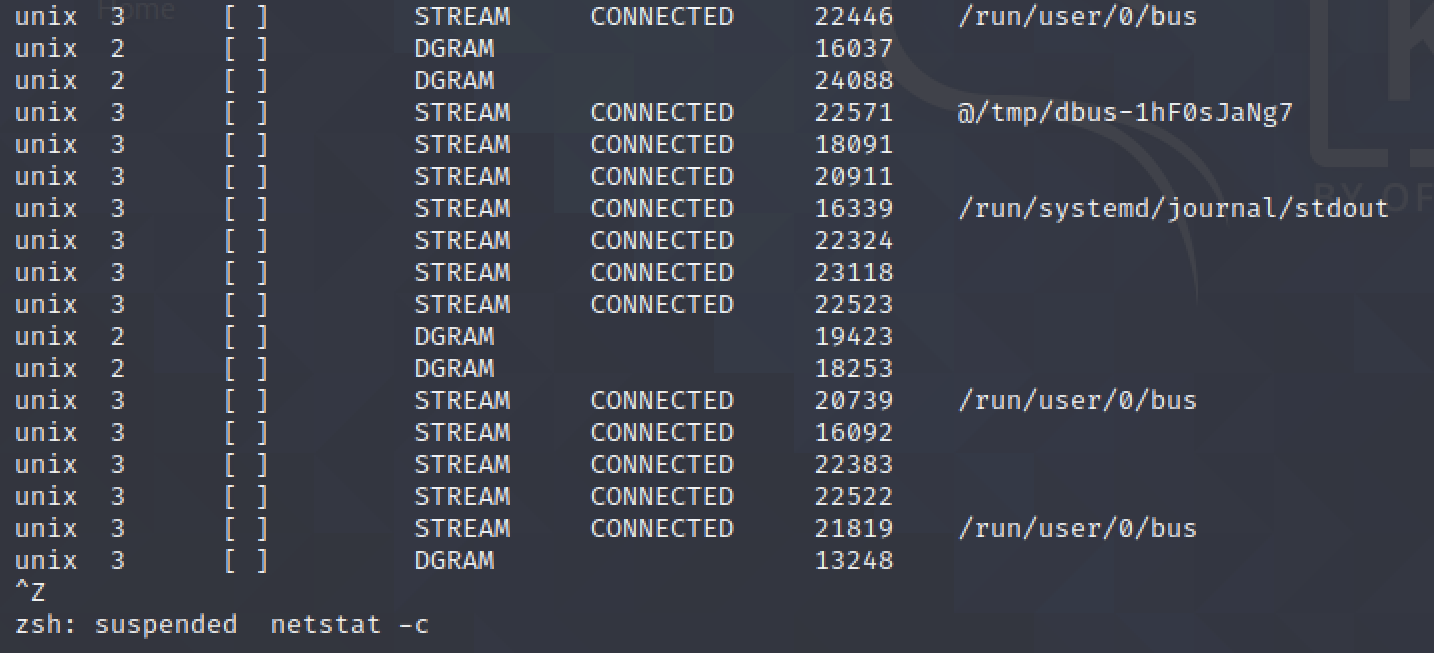
$ netstat -c
Produces the output same as netstat -a for every second and the command has to be terminated manually using ctrl + shift + z.
Code
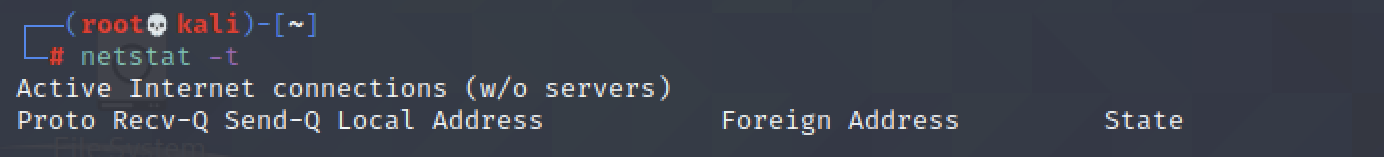
$ netstat -t
Shows all TCP ports.
In order to get an output for this command, let’s start ssh in kali and connect my host to kali. In kali terminal, type the following code.
Code
$ service ssh start
$ ifconfig
Code
$ ssh root@<IPAddress>
NOTE: By default, ssh to root is not permitted because it is dangerous since it gives full privileges to the user and hackers can easily exploit the host and it's network once a backdoor is created in the host. To ssh with root access, the sshd_config file in etc/ssh directory has to be modified.
Now, type netstat -t.
Code
$ netstat -u
Shows all UDP ports.
Code
$ netstat -r
Shows the kernel IP routing table.
Code
$ netstat -v
Produces the same output as netstat -a with an extra set of lines as given below.
Code
$ netstat -l
Shows all the listening ports.
Code
$ netstat -lp
Here netstat -p is used with the l command as netstat -lp. '-p' gives the PID / Program name column which was not there before and '-l' shows the listening ports only.
Code
$ netstat -o
Produces same output as ‘-a’ with an additional timer header.
Code
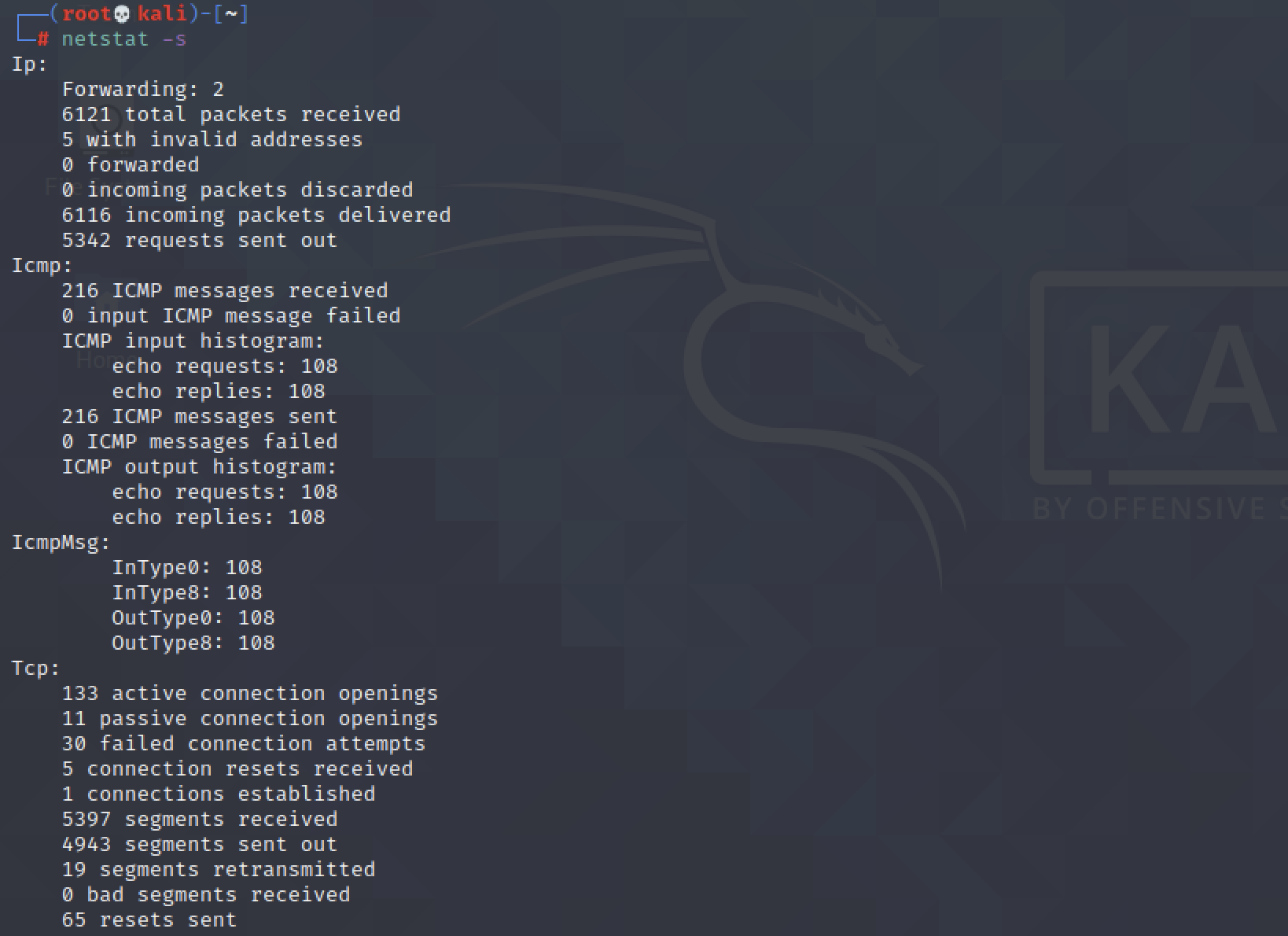
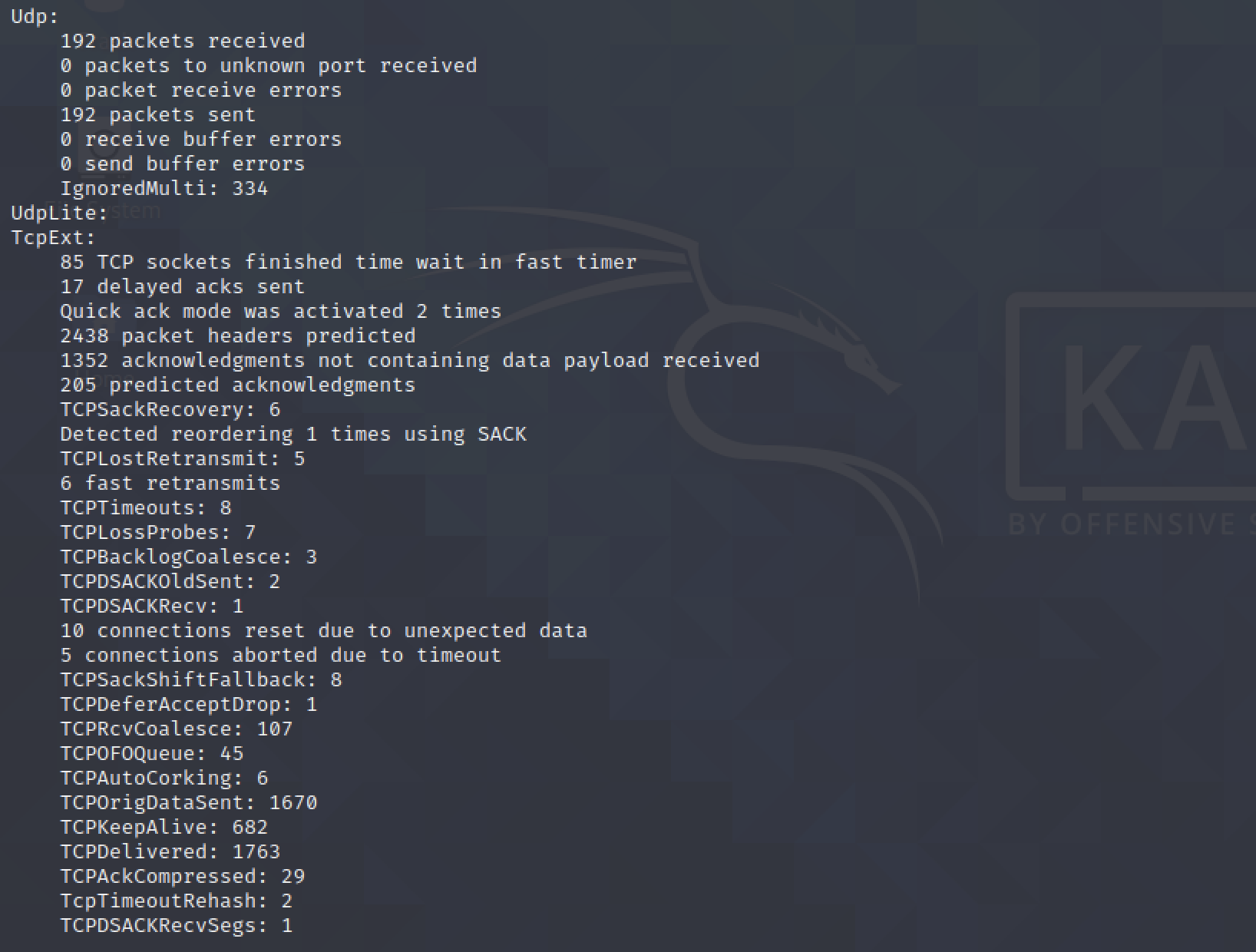
$ netstat -s
Shows network statistics.

Code
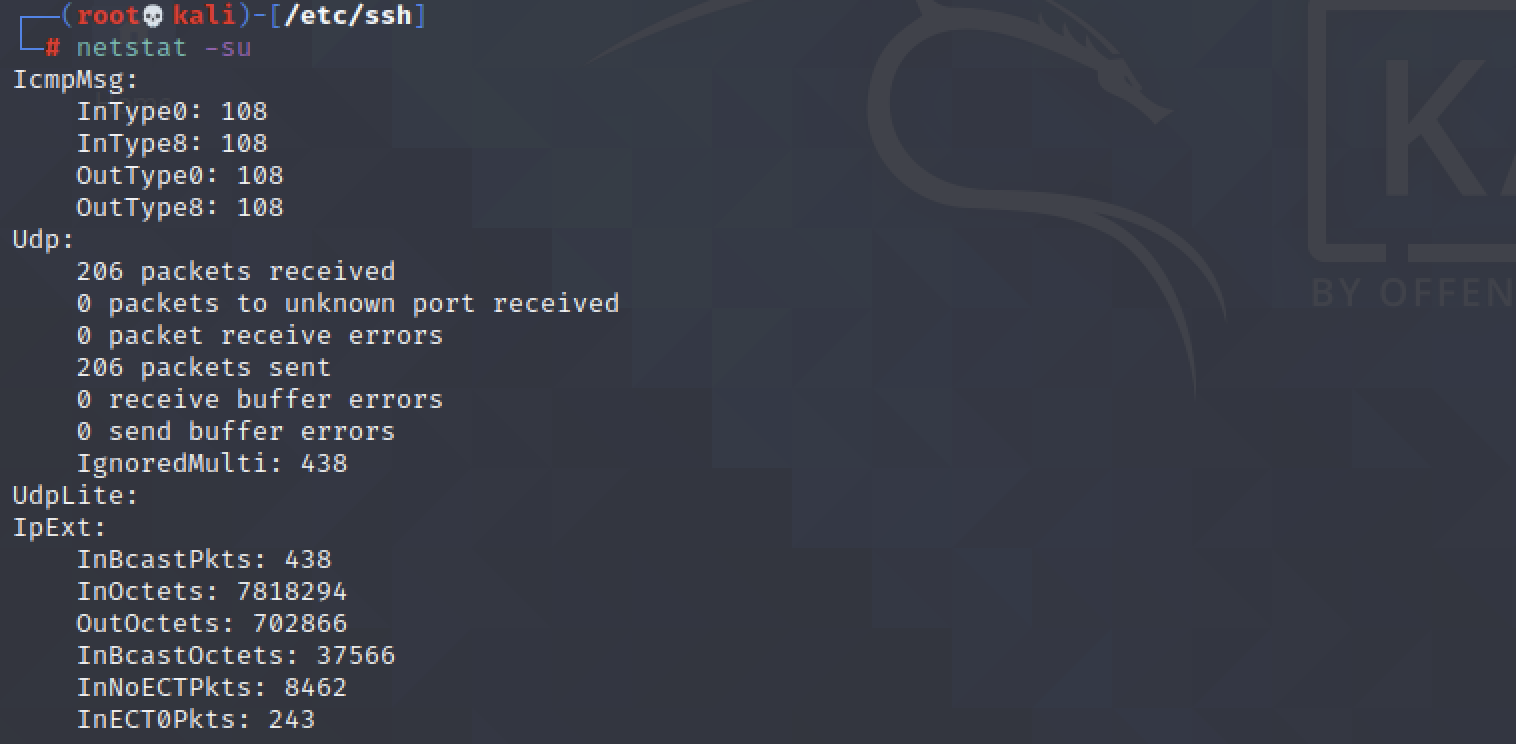
$ netstat -su
Shows the statistics of UDP ports only.
Code
$ netstat -i
Shows kernel interface table.
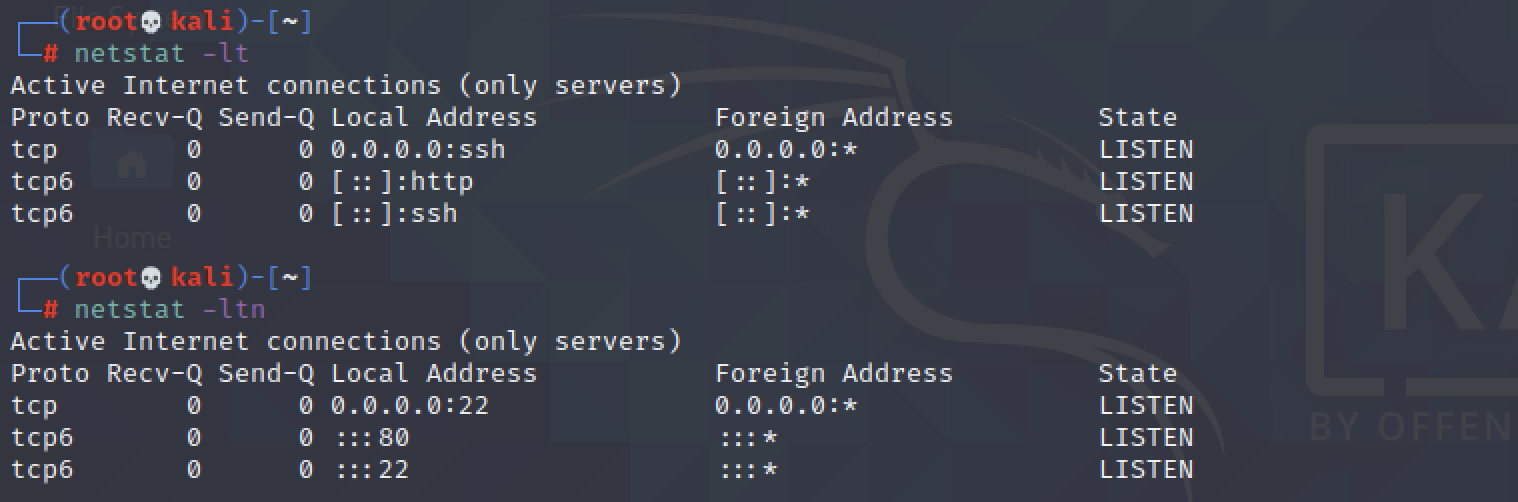
Difference while using netstat -n:
Code
$ netstat -lt
$ netstat -ltn
USING NETSTAT WITH GREP:
To find whether the host is hosting ssh server, we can use ‘grep ssh’ or ‘grep 22’, since 22 is the default port number for ssh.
Code
$ netstat -atnp | grep 22
$ netstat -atnp | grep ssh
Likewise to find whether the host has a http connection, we can use ‘grep http’ or ‘grep 443’ since 443 is the port number for web browser communication.
Code
$ netstat -atp | grep http
Output when web browser is not running.
Output when web browser is running.
In the next part, let's analyse the output of netstat command.


















1 Comments
Very useful ✌️ nice 🙂
ReplyDelete