Machine Learning is an incredibly useful tool when it comes to cybersecurity, allowing for
advance detection and protection mechanisms for securing our data. One particularly potent machine
learning concept is the Generative Adversarial Network (GAN).
What is GAN?
General Adversarial Network(GAN) can learn to generate new samples from the input data set, compare them with the labeled real-world data, and decide whether they are realistic or fake. GAN consists of two neural networks, a generator and a discriminator.
-The GENERATOR learns to generate plausible data. The generated instances become negative training examples for the discriminator. The generator model maximizes the classification error rate.
-The DISCRIMINATOR learns to distinguish the generator's fake data from real data. The discriminator penalizes the generator for producing implausible results. The discriminator model minimizes the classification error rate.
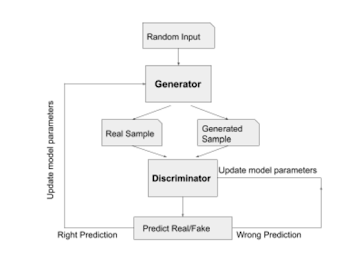
GAN is a generative approach used in many applications, such as the generation of human faces or cartoon characters and many other photographic applications. this method can also generate fake information, images, etc., which is not acceptable by society but inevitable. Though GAN has a vast amount of applications in the computer vision field, it has significant usage in cybersecurity too. The task of detecting different kinds of cyberattacks such as anomaly detection, denial of services (Dos), Distributed DoS, Man-in-the Middle, phishing, injection attack etc., has been eased with the implementation of different kinds of generative adversarial networks. Cyberattacks measures should be at least one step ahead of cyberattacks to differentiate between real or fake information, images or videos.
Application of GAN in Cybersecurity
Anomaly Detection
In a data distribution, the data patterns which don't follow the normal behavior of the dataset, are called anomalous data. Anomaly detection is to detect those anomalous data in order to tackle critical incidents such as technical glitches, structural defects, security errors, and even bank fraud.

Using AnoGAN architecture: Standard GAN is used in AnoGAN, which only tarin on only positive samples, to learn mapping from the latent space representation to realistic sample and this learned representation is used to map new, unseen, samples back to latent space. By training GAN on normal samples generator may learn manifold X of normal images and when an anomalous image is encoded it reconstruction can be non-anomalous. During test time the latent vector is found which maps the test images to its latent representation. To denote anomalous region the reconstructed image is used and this is the area where the difference between the input and the reconstructed image will show anomalies.
Phishing
Phishing is one of kind of cybercrime in which malicious actors, disguised as a legitimate institution, send mail or text messages to targets to lure them to provide personal or confidential information such as banking or credit card details, passwords. Though the performance of machine learning algorithms is quite promising in preventing phishing attacks, it couldn't go beyond a certain limit as the efficiency of ML algorithms most of the time depends on the training data. To mitigate this limitation, many adversarial methods have been introduced as it is augment existing datasets.
It consists of a generator network which creates synthetic phishing features for training the discriminator together with real phishing features, and a discriminator network which determines if the features are indictive of a legitimate phishing attack.
Distributed Denial of Service(DDoS) and Intrusion Detection
A DDoS attack is a cyber-attack where the connection of a host to its network is being disrupted by sending too many requests to the targeted machine which makes the system overloaded and thus becomes temporarily or indefinitely unavailable for its legitimate users. It has become a widespread threat to the security and integrity of network these days. In recent years many ML- based network intrusion detection systems have been introduced to prevent this attack. In these techniques, one of the most common drawbacks is to generate crafted input data to mislead classification and the prediction mechanisms. Adversarial training has been introduced to overcome this by many researchers. In GADoT, proposed by Abdelaty leveraged a GAN to generate adversarial DDoS examples for training data to detect both SYN and HTTP flood attacks. The evaluation of this training model is done without the knowledge of the victim model, which makes it apart from other similar approaches.
How to keep data reliable
Any data is a source of an attack scenario. The distinction between real-world and fake data is easier to manage with the GAN approach. An advanced generative model that has already learned to generate data with a low classification error rate can generate fake data to deceive any system and check whether the target system is robust enough against synthetic attacks. GAN could be a tool to argue for assessors about resilience of systems against cyberattacks. A process not only for identified attack scenarios that criminals do not yet use. This approach is a new trend that will soon significantly impact safety and security standards and development activities.
GAN approach to ensuring safety and security in self-driving car technology
Hacking unmanned vehicles are more critical than the vehicle where the driver is present in the car. Depending on the type of the attack, attackers can modify vehicle navigation, reactions, collect specific sensor data, etc. Learning from existing attacks based on attacks already observed. GAN can generate realistic traffic scenarios to improve system validation or robust system behavior.
Few things to keep in mind about GAN in Cybersecurity
Password Cracking
GAN can be employed to crack passwords by generating probable password candidates based on the patterns observed in the existing passwords. This highlights the importance of strong, unique passwords and multifactor authentication.
Privacy and Confidentiality
While GANs have shown great potential in cybersecurity, their also raises privacy concerns. They can also be used to create deepfake content, making it difficult to trust audio, video, or text-based information. Protecting against such misuse is a growing challenge in the field.
Challenges
GANs are not without challenges in cybersecurity, They can sometimes generate false positives or false negatives in anomaly detection. Moreover, GAN-generated attacks can be challenging to detect by traditional cybersecurity mechanisms.
In conclusion, GANs offer significant advantages in enhancing cybersecurity, from improving anomaly detection to creating deceptive defenses and aiding in malware analysis. However, their application also comes with ethical and privacy considerations that must be addressed as the technology continues to evolve. As cyber threats continue to grow in sophistication, GANs will play an increasingly important role in bolstering the defense and resilience of systems and networks.







0 Comments