Why should you hunt for subdomains for a website as a penetration tester/ bug bounty hunter?
But from a penetration tester or bug bounty hunter's point of view, it all boils down to finding subdomains that are juicy, such as dev.companyName.com, test.companyName.com, etc. which as the names suggest shouldn’t be available to the end users. So taking down these kinds of websites is very important from a security point of view. And especially from a bug bounty point of view, if you manage to find a site that has no HTTPS protection or some kind of development website, you have higher chances of getting a really good vulnerability, especially one from OWASP Top 10 ones. Reconnaissance is an integral part of bug bounty hunting.
There are
multiple tools to achieve this task. One legendary tool which really stands out
from the crowd is OWASP amass, but it’s a little complex to use and simpler
tools are available for similar uses. Let’s see the simpler tools first to have
a better understanding of hunting subdomains for a website.
Let's try to
list the subdomains for the website Tesla, owned by the billionaire Elon Musk(this particular bug bounty program is available on bugcrowd, therefore everything done below is ethical).
Tool 1: sublist3r
This is one of the easiest tools to use, just give the name of the website and it will return you with 1st,2nd and 3rd level subdomain websites!
To install, in case not available:
Let's hunt some
subdomains!
Sublist3r comes
with a variety of options one can use. Our aim is to find subdomains therefore
we use -d to define the domain. You can always use -h for help.
So to find
subdomains of tesla we need to type:
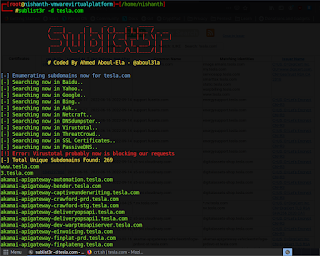
$ sublist3r -d tesla.com
Where -d represents domain name.
After running
the command we get,
As you can see
above it searches it on 11 different search engines and returns the result. It
found around 200 websites when I ran it for 15 min. But we cannot assume all
of them are alive.
It is necessary to see what all websites are
alive/dead to narrow down our findings. One can easily code a python script for
probing websites, or can use TomNomNom’s HTTP Probe from GitHub: tomnomnom/httprobe:
Take a list of domains and probe for working HTTP and HTTPS servers
(github.com)
Tool 2: crt.sh
On clicking the search button we get the results:
As you can see
it can also gather certificates of SSL and TLS for a subdomain and the issuer
name too, which can be useful for us in multitudinous ways.
You do need to
remove dead websites from the findings, having them is not useful for us in
any way.
Let's move to
the 3rd and most powerful tool. This is very useful for bug bounty
hunters
Tool 3: OWASP amass
A very powerful tool written in Go, it includes
DNS enumeration, Network mapping, Brute Force, Name permutation, Reverse DNS
Sweep, and Scraping.
During the
presentation of OWASP amass by Jeff Foley on YouTube, who is the core developer of
this tool, he showed this…
Yes, this
question “can you provide a list of all your systems?” is generally encountered
by ethical hackers during pentesting a network inside an organization and can
be avoided if one masters this tool, and it's really simple to use!
But for our
topic, we will stick to the commands which serve our blogs topic “hunting
subdomains”.
Amass has 5
main subcommands that can be used(as of the 2021 release):
1.
Intel
– Discover targets for enumerations
2.
Enum-
Perform enumerations and network mapping
3.
Viz-
Visualize enumeration results
4.
Track
– Track differences between enumerations
5.
Db
– Manipulate the amass graph database
We will be
seeing enum and db sub-commands for our purpose.
As usual, while
seeing a new command, type -h for help.
Let's hunt subdomains again!
These subdomain and their details are saved in your local HDD at amass’s database directory after execution has been completed. To read it:
We get all the
websites found related to the given query.
Here, -names
and -d is used to list out all names indexing to tesla.com.
This should be
enough for anyone who is a beginner to this tool to get their hands dirty.
As I have mentioned before, amass is a little bit complex to use, but for the blog’s purpose, the above commands are more than enough.
Right now a great tool called "dome" is becoming popular.. it's totally worth checking out! link: https://github.com/v4d1
Many bug bounty hunters, like STÖK, use similar kinds of recon methodology to gather valuable subdomains and then spend days hunting on them.
But if
you want to learn more you can refer to the below resources:
OWASP amass
presentation: https://youtu.be/HaVEH1vFiN0 ,
Tutorial sheet
at Github: Amass/tutorial.md at master ·
OWASP/Amass (github.com) .
Happy hunting!
Connect with me on LinkedIn!










0 Comments