What is network sniffing?
Network sniffing monitors the flow of data over different computer lines using a software tool that is referred to as a network sniffer. This sniffer can be a closed software package or a hardware device that is governed by the appropriate software. As data flows past the sniffer, the tool takes a picture of the data but does not alter or redirect that data. It is a tool that is also used by hackers togain vital information. It is possible for a network sniffer to capture passwords as they flow by.
Sniffing is the process in which all the data packets passing in the network are monitored. Sniffers are usually used by network administrators to monitor and troubleshoot the network traffic. Whereas attackers use Sniffers to monitor and capture data packets to steal sensitive information containing password and user accounts. Sniffers can be hardware or software installed on the system.
What is network spoofing?
The boiled down definition of network spoofing is getting access to computer data that you have not been authorized to access. To correctly perform network spoofing, the hacker or unauthorized user needs to assume the identity of another computer or computer program.There are different types of spoofing including e-mail spoofing, network spoofing, and IP spoofing. A hacker who wished to use the spoofing method must find the identity of a trusted computer or program, assumethat identity, and gain access to private information. Since the spoofed ID is trusted, the hacker usually has no trouble entering restricted areas.
Spoofing is the process in which an intruder introduces fake traffic and pretends to be someone else (legal source or the legitimate entity). Spoofing is done by sending packets with incorrect source address over the network. The best way to deal and tackle with spoofing is to use a digital signature.
Though Kali Linux comes packed with many tools for sniffing and spoofing the ones listed below, are mostly used by attackers these days.
Top three Network sniffing and spoofing tools
1. Wireshark
2. Smartsniff
3. Mailinator
Network sniffing with wireshark
Wireshark Top Filters
1. Protocol Filter
2. Port Filter
3. IP Address Filter
4. Source and Destination Filter
5. Multiple Protocol Display Filter
6. Removing Unwanted Packets
7. TCP, HTTP stream
8. Contains filter
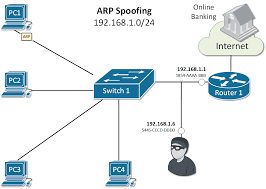
ARP Spoofing Using Bettercap.
- ARP is short for Address Resolution Protocol and ARP spoofing is where a hacker or any other unauthorized person sends false ARP messages to your computer or network.
- There is usually a link between the hacker's MAC address and a legitimate IP address.
- Once this connection is made, the hacker receives any information sent to the legitimate IP address.
- The good news is that this type of spoofing can only occur on local networks that use ARP. A hacker's reasons for using this spoofing method vary and may include stopping data, altering it, or interception of key messages










0 Comments