Hello Readers!
“You never appreciate your anonymity until you don’t have it anymore.”To safeguard this anonymity, a new term, VPN has been added to our lives and has verily become indispensable now.
What is VPN?
For readers unfamiliar with this term, VPN stands for “Virtual Private Network” and used to establish a protected network connection when using public networks. It encrypts your internet traffic and disguise your online identity. And ultimately making it more difficult for third parties to track your activities online and steal data, and helps you to maintain anonymity on the internet.
VPNs became this important as it allows users to bypass geo-blocks, annoying firewalls, and government censorship, to protect their data against mass surveillance, advertisers, and hackers and to secure their freedom of speech online too.
But the now the questions pop on the credibility of these VPNs, "Will a VPN guarantee your digital anonymity? Can someone still eavesdrop on your browsing activities?".
The answer is may be "Yes" or might be "No". 🤔
But before diving into this answer, let’s first understand how does a VPN work. Your only identity on this internet is your IP address. When you use a VPN, it establishes a secure connection between you and the internet, ultimately disguising your public identity on the internet, ensuring your anonymity. It redirects the data traffic through a specially configured remote server run by the VPN host. This acts as a mask on your identity, meaning whatever you surf online with a VPN, the VPN server becomes the source of your data, rather than your original IP. The image below will let you easily understand how VPNs ensures your privacy.
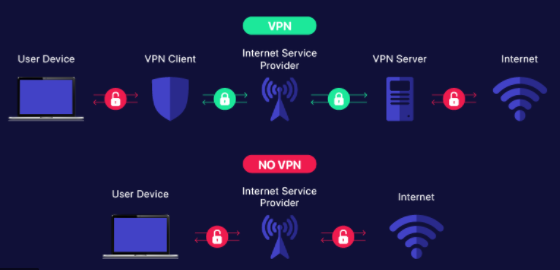
These VPN servers have their host servers set in various countries. So, when you connect to any of those host VPN servers and visit any start browsing, then for the requested URL host, your location is detected to be same as that of the VPN host server, rather than your actual current location. Any website which requests to access your location, it just makes a query in a global database where each IP address is mapped to a location. So, whatever VPN IP address it receives, it just queries it in the database and customizes the content displayed to you according to your IP’s location, like you must have experienced this with e-Shopping, Netflix etc.
If this fails, then can you be tracked?🤨
Although VPNs are safe, but the inefficient IP handling mechanism reduces their efficiency and make u you vulnerable of being exposed publicly even after using a good VPN.
Some of the most common factors risking your anonymity are:
VPN IP addresses: Most of these VPN services have been using the same set of IP address ranges for a long time. So, various location critical websites like Netflix etc. have set-up their own VPN server databases, which lists all the prominent and obsolete VPN IPs. So, when you use any such VPNs and your IP matches in their database, you will be restricted to access the content of that particular website. This won’t expose your original identity, but the soul purpose of being anonymous is lost.
Port number: Various VPN protocols use specific port numbers to establish the connection. For example, in case of OpenVPN, for UDP it usually uses port number 1194, while for TCP it typically uses 443. So, these port numbers can give away the type of VPN connection you’re using.
VPN Logs: Your VPN service provider may provide you with no-logs policy. In this policy the VPN provider doesn’t store any logs of your VPN sessions. So, in case any DNS leaks happen or the government approaches them, then they are gonna just receive a big 👎. But in case your VPN doesn’t follow this policy then your anonymity is ensured only till there’re no DNS leaks or you are away from any legal enquiry.
Some VPN services agree to install backdoors for the government, allowing agencies to monitor user traffic. This is specifically for those countries where only government approved VPNs are allowed to operate, like China. So, VPNs and anonymity is all a big a hoax with VPNs don’t follow this no-log policy.
Deep packet inspection (DPI): DPI is a process of inspecting the structure of each data packet in the network traffic. This is prominently used for blocking spams or malwares. However, it can also be used to identify VPN traffic. This is what the government of China uses to block the unapproved VPNs.
Google Tracking: If you connect to a VPN, and still continue to use your google account for online surfing, then VPN is just solitary. Because google keeps track of all your online activities. Since a VPN merely changes your virtual location, it might look like you’re accessing the websites from a different region, but Google will still be able to determine it’s you. And if you’re day dreaming about privacy with incognito mode in google chrome, then buddy wake up! Google will still track you using cookies and browser foot-printing. The best way to minimize tracking is by using privacy-oriented browsers and cookie blockers.
Business and Commercial VPNs: If you are using a business VPN provided by your employer, then you are anonymous for the rest of the world except your employer and the corresponding VPN service provider. These business VPNs don’t follow no-log policy and provides backdoor access of your online session to your employer, so here privacy and anonymity is indeed fictitious. But if you are using commercial VPN on top of your business VPNs then, your employer needs to do some simple extra to-dos, like installing keyloggers into your system, and everything fails subsequently then. Therefore, it's advisable not to use your employers' system for any personal surfing.
Apart from these cookies, browser finger-printing, malwares and spywares are often used to make these VPNs fail.
Till now, you must have got an insight about VPNs, its working and how these privacy guards can be defeated.
Take a deep breath and relax, solutions are waiting for you! 😀
Head on to my next blog for the check measures and solutions to ensure your privacy and anonymity online. >>Is “P” in your VPN public? (Part-2)




0 Comments