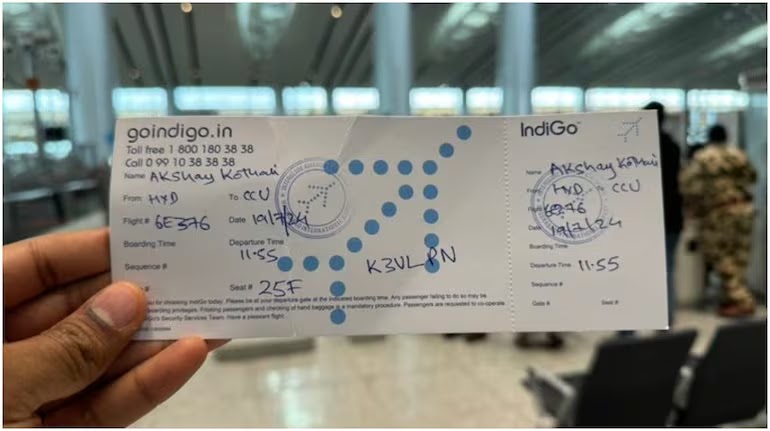
As we digitalize more and more aspects of our lives, we are presented with opportunities and challenges equally. Who would’ve expected we’d look at a blue screen on a refrigerator? Or a handwritten boarding pass for a flight? Or an early weekend since systems were impacted on an unprecedented scale!
Microsoft faced a widespread outage on July 19th, 2024, leading to disruptions across multiple services and leaving users worldwide experiencing the 'Blue Screen of Death' (BSoD). In this blog, we shall be analyzing the issue in detail.
A smart refrigerator affected by BSoD
The viral image posted by a passenger on the IndiGo The BSoD is a critical error screen on Windows PCs that halts all operations and displays an error message. This occurs when the system encounters a severe issue, often leading to an unexpected restart and potential data loss.
CrowdStrike is a well-known cybersecurity firm, and its Falcon Sensor software is designed to protect Windows systems from cyberattacks. On July 19th, CrowdStrike warned users about a bug related to the Falcon Sensor that was causing Windows systems to crash with BSOD errors. Users reported problems accessing essential services such as Outlook, Microsoft Teams, and various Azure-hosted applications. Businesses reliant on these services faced productivity losses, delayed communications, and operational slowdowns. Despite rolling back the update, many systems continued to be affected.
Why did it happen?
CrowdStrike admitted that a sensor configuration update for Microsoft Windows systems in its antivirus software was the reason behind the issue. The faulty update was caused by CrowdStrike's Falcon Sensor to malfunction and conflict with the Windows system. The cause of the incident was not a cyberattack, the company stressed.
How did cybercriminals exploit the vulnerability?
CrowdStrike warned that threat actors were attempting to exploit the situation to distribute Remcos RAT to its customers in Latin America under the guise of providing a hotfix. The attack chains involve distributing a ZIP archive file named "crowdstrike-hotfix.zip," which contains a malware loader named Hijack Loader (aka DOILoader or IDAT Loader) that, in turn, launches the Remcos RAT payload. The archive file also includes a text file ("instrucciones.txt") with Spanish-language instructions that ask targets to run an executable file ("setup.exe") to recover from the issue.
CrowdStrike, in its blog, released a list of websites they had identified, as impersonating the company, attempting to provide fixes. Other kinds of activity observed range from impersonating CrowdStrike staff in phone calls to posing as independent researchers and claiming to have evidence the technical issue is linked to a cyber attack.
List of phishing websites
The cybersecurity departments of various countries also issued warnings:
The solution?
Yes, the obvious classic one- turning it off and on over and over again! However, users with in-depth technical knowledge can delete a certain file on their computer. a CrowdStrike employee shared on social media.
The Indian Computer Emergency Response Team (Cert-In) which is the government's nodal body for all cybersecurity-related matters said that though the fix had been issued, users should boot their devices into safe mode or in the Windows recovery environment.
In the recovery environment, the user should "navigate to the C:\Windows\System32\drivers\CrowdStrike directory, locate the file matching "C-00000291*.sys", and delete it".
After deleting the file, users can restart their devices normally.
Though CrowdStrike has issued its fix now, it will have to be applied separately to each and every device affected. Computers will require a manual reboot in safe mode.
Does it affect you and me?
No, the software responsible for the outage is generally used by businesses, which means that most of our personal computers won't be impacted. We generally use built-in antivirus software or security products offered by companies such as Norton and McAfee that are much more popular.





0 Comments